EU Cyber Regulations
In an era where digital transformation is pivotal, cybersecurity has become a critical concern for businesses and governments alike. The European cybersecurity landscape is rapidly evolving, driven by a need to protect digital infrastructure and ensure the safety and privacy of data. This post aims to provide an overview of the key emerging regulations, acts, directives, and standards shaping cybersecurity in Europe.
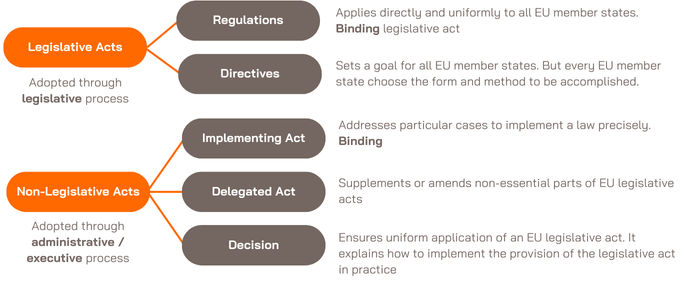
1. Regulations, Directives and Acts:
With the upcoming European regulations regarding cybersecurity, the EU aims to establish an efficient and robust framework to address future challenges and protect the community, especially consumers of emerging technologies. Let’s clarify and summarise the different type of legal instruments available at the European level:
2. Product cybersecurity in EU:
In terms of product cybersecurity several initiatives are present in the European Landscape.
2.1 Cyber Resilience Act (CRA)
The Cyber Resilience Act (CRA) is a legislative initiative by the European Union designed to enhance cybersecurity standards for products with digital elements (PDEs), including both hardware and software. The Act aims to ensure that such products meet specific cybersecurity requirements throughout their lifecycle, from design to market placement and beyond.
- Baseline Security Requirements: Ensuring that connected products meet basic cybersecurity standards.
- Vulnerability Handling: Mandating procedures for handling and disclosing vulnerabilities.
The CRA was politically agreed upon in late 2023 and is expected to be fully adopted by the European Parliament in early 2024. The Act includes a phased implementation, with most obligations becoming enforceable over a 36-month period, allowing stakeholders time to adapt. However, vulnerability and incident reporting requirements will come into effect within 21 months of the CRA's entry into force.
2.1.1 CRA Challenges and Applus+ Laboratories view
Experts generally view the CRA as a significant step forward in reinforcing EU cybersecurity. It aligns with other EU regulations like the NIS2 Directive and the AI Act, aiming to create a cohesive cybersecurity framework across different sectors. However, there are concerns about the Act's stringent reporting requirements and potential overlaps with existing laws, which could impose additional burdens on manufacturers and importers. Some experts advocate for more clarity and flexibility in the reporting obligations to avoid overwhelming smaller companies and stifling innovation.
The concern about having to pass several certifications for a single product around the world, which would increase the effort and costs, is significant. That’s why CRA standardisation is crucial. Nevertheless, there are significant challenges including harmonising and updating existing standards or creating new ones to intrinsically meet the essential requirements of the CRA. In addition, the European Commission draft standardisation request mentions 41 new standards; this could be an issue due to the lack of experts in the community.
Additionally, effective monitoring and enforcement mechanisms will be necessary to ensure compliance even if concerns about the penalties that will be applied are present among the manufacturers. This includes establishing robust oversight bodies and providing them with the necessary resources to perform their duties.
More information on CRA and Applus+ related services
- An overview of EU’s Cyber Resilience Act
- EUCC: Towards a new EU Common Criteria Scheme
- EUCC certification services
- Applus+ Cyber Resilience Certificate of Conformity
2.2 Radio Equipment Directive (RED) and RED Delegated Act
The Radio Equipment Directive (2014/53/EU) establishes a regulatory framework for placing radio equipment on the EU market, covering aspects like safety, health, electromagnetic compatibility, and the efficient use of the radio spectrum. It aims to create a single market for radio equipment, ensuring these products are safe and do not interfere with other electronic equipment.
The Delegated Act to the RED, specifically addressing Articles 3.3 (d), (e), and (f), introduces new cybersecurity requirements for wireless devices. These articles cover:
- Network protection – Article 3(3) d: Ensuring that radio equipment does not harm the network or misuse its resources.
- Protection of personal data and privacy – Article 3(3) e: Protecting personal data and privacy of users.
- Protection from monetary fraud – Article 3(3) f: Implementing safeguards to prevent monetary fraud.
The RED Delegated Act is a supplementary legislative measure under the European Radio Equipment Directive (RED). It provides detailed rules and criteria for specific technical aspects and requirements that radio equipment, including IoT devices, must meet to be placed on the market within the EU. The RED Delegated Act addresses areas not covered in detail by the main directive, ensuring a comprehensive regulatory framework.
2.2.1 RED Challenges and Applus+ Laboratories view
Experts view the RED Delegated Act as a critical step towards enhancing the cybersecurity of wireless devices, aligning with broader EU cybersecurity strategies. By requiring manufacturers to integrate robust cybersecurity measures, the act aims to mitigate risks associated with increasing connectivity and cyber threats. However, there are concerns about the challenge of the readiness of harmonised standards and the potential burden and complexity to implement on manufacturers, especially SMEs and companies with low cybersecurity experience, to meet these new requirements.
As of now, since the RED delegated act will be mandated for compliance from August 1st, 2025, the EN18031 (parts 1, 2, and 3) has recently been voted as the harmonized standard for RED compliance.
The cybersecurity measures proposed are seen as necessary to protect consumers' data and ensure the integrity of communication networks. There is a widespread belief that standards to comply with the RED directive will be superseded by the CRA standards.
2.3 Cyber Security Act (CSA)
The act introduces an EU-wide cybersecurity certification framework for ICT products, services, and processes. This framework aims to enhance trust and security in the digital market by ensuring that products and services meet consistent and recognised security standards.
One of the schemes under the CSA is the recent EUCC. The EUCC implementing act has already entered into force, setting the rules for the scheme stakeholders. Other schemes to come include the EU5G and the EUCS, the latter being expected by Q4 2024.
Other schemes that need to be prioritised include the European Digital Identity Wallets and Managed Security Services according to the SWD (Staff Working Document) for the Union Rolling Work Programme for European cybersecurity certification.
2.3.1 CSA Challenges and Applus+ Laboratories View
Experts generally view the CSA as a crucial step towards enhancing cybersecurity within the EU. By establishing a unified certification framework, the CSA helps increase trust in digital products and services, facilitating smoother cross-border trade and boosting the Digital Single Market. However, there are ongoing discussions about refining ENISA's mandate and improving the efficiency of certification processes to better meet the evolving cybersecurity landscape as well as efficiency in creating new schemes.
The EUCC scheme has already been launched, marking a significant milestone as the first successful scheme under the CSA. This is very positive news. In any case, there is still some work to do as site certificates are not inside of the EUCC, the accreditation requirements for CBs are still not released and the accreditation requirements for ITSEFs still need some refinements regarding interpretations.
Furthermore, other schemes are in the pipeline, like the EU5G scheme. This new scheme may require an additional standardisation work in order to be aligned with other international 5G certification schemes, such as GSMA, so manufacturers can have a unified scheme that encompasses all security requirements for 5G products.
Additionally, political debates, such as those concerning the EUCS cloud services certification scheme, highlight the complexities of integrating national sovereignty requirements with EU-wide standards. The sovereignty requirements have been a point of contention, with some industry stakeholders and member states viewing them as potentially protectionist. The compromise to focus on transparency has been welcomed as a balanced approach to address these concerns.
2.4 Artificial Intelligence Act
EU Artificial Intelligence Act is the world's first comprehensive regulatory framework specifically designed to address the risks and challenges associated with artificial intelligence.
It introduces a comprehensive framework to ensure that AI systems are safe, transparent, and respect fundamental rights. The Act classifies AI systems based on their risk levels: unacceptable risk (prohibited), high risk (strict regulation), limited risk (transparency requirements), and minimal risk (largely unregulated).
While primarily focusing on AI, this act includes provisions relevant to cybersecurity, particularly for category of high-risk AI systems. It sets the provisions for:
- Risk Management: Obligations for managing cybersecurity risks in AI systems.
- Security Requirements: Ensuring AI systems are secure by design and resilient against attacks.
The AI Act was adopted by the European Parliament in March 2024 and is expected to be fully applicable within 24 months, with some parts coming into force sooner. This includes an immediate ban on AI systems posing unacceptable risks and the introduction of codes of practice within nine months.
2.4.1 AI Act Challenges and Applus+ Laboratories view
Some experts, particularly from start-ups and SMEs, express concerns that the AI Act could impose substantial regulatory burdens. They fear this might disadvantage European companies compared to their American and Chinese counterparts by creating additional barriers to innovation.
The focus now shifts to the effective implementation and enforcement of the Act. This includes ensuring that the AI Office has the necessary resources and that the AI Liability Directive complements the AI Act effectively. There is still a long journey and harmonised standards to cover this need.
2.5 European Digital Identity Framework
The European Digital Identity Framework, also known as eIDAS 2.0, is an updated regulation aimed at providing EU citizens and businesses with a secure and standardized digital identity solution. This initiative builds on the original eIDAS regulation from 2014 and seeks to address its limitations by introducing a more flexible and comprehensive framework. It includes:
- EIDAS Regulation: Enhanced security measures for electronic identification and trust services.
- Digital Wallets: Providing secure and interoperable digital identity solutions across the EU.
The European Digital Identity Framework was adopted by the European Parliament and the Council in early 2024 and is expected to come into force by the end of the summer of 2024. Member States are currently working on implementing the framework, with the first digital identity wallets expected to be available in 2025
2.4.1 European Digital identity challenges and Applus+ Laboratories view
Experts appreciate the focus on security and the harmonised approach to technical architecture, which is expected to enhance the efficiency and security of digital identity solutions across the EU.
The new framework is seen as a significant step towards empowering citizens with trusted and secure digital identities, potentially increasing the adoption rates of digital identity services.
Some of the challenges is that there are concerns about the complexity of implementing such a comprehensive framework and ensuring interoperability among different national systems and the method by which these wallets will be certified given the importance of the product and the data they handle.
Are there other regulations to be implemented at the same time?
Yes, there are other regulations such as DORA and NIS2 that also implement and interact with the EU cybersecurity framework landscape.
While NIS2 focuses more broadly on critical sectors and their cybersecurity practices, DORA specifically targets financial entities and includes explicit requirements for penetration testing to ensure digital operational resilience. These regulations align with established standards and best practices, underscoring the need for a proactive and comprehensive approach to cybersecurity.
What about other regulations from China and USA?
But what about cybersecurity regulations around the world? Several frameworks, laws, frameworks, guidelines, acts are present around the world.
Here are some of the relevant cybersecurity regulations in China:
- Cybersecurity Law
- MLPS 2.0
- Cybersecurity Review Measures
- Cryptography Law
- Radio Regulations, Administrative Provisions on Radio Frequencies
- Guidelines for AI Ethics, New Generation AI Development Plan
- eID system, Real-Name Registration System
Here are some of the relevant cybersecurity regulations in USA:
- CISA
- FISMA
- NIST Cybersecurity Framework, Executive Order on Cybersecurity
- FCC Rules and Regulations
- AI Initiative Act, Algorithmic Accountability Act
- NSTIC, Real ID Act
Experts generally view the EU’s regulatory frameworks as setting a high bar for digital governance, ensuring that technologies are developed and used responsibly. However, the interaction with US and Chinese regulations highlights the challenges of differing approaches.
The EU’s comprehensive and stringent regulations can sometimes lead to higher compliance costs and potential innovation stifling, while the more flexible US approach and the stringent but centrally controlled Chinese model each have their own sets of benefits and drawbacks. The key is finding a balance that promotes innovation while ensuring security, privacy, and ethical standards!
At Applus+ Laboratories, we are here to guide and support you through the certification process, to verify your product meets compliance standards.